Your guide to everything STIR and SHAKEN
STIR (Secure Telephony Identity Revisited) and SHAKEN (Secure Handling of Asserted information using toKENs) are the frameworks that promise to prevent the completion of illegally spoofed calls.
Overview
STIR/SHAKEN uses digital certificates, based on common public key cryptography techniques, to ensure the calling number of a telephone call is secure. Each telephone service provider obtains their digital certificate from a certificate authority who is a trusted authority. The certificate technology enables the called party to verify that the calling number is accurate and has not been spoofed.
STIR/SHAKEN work flow
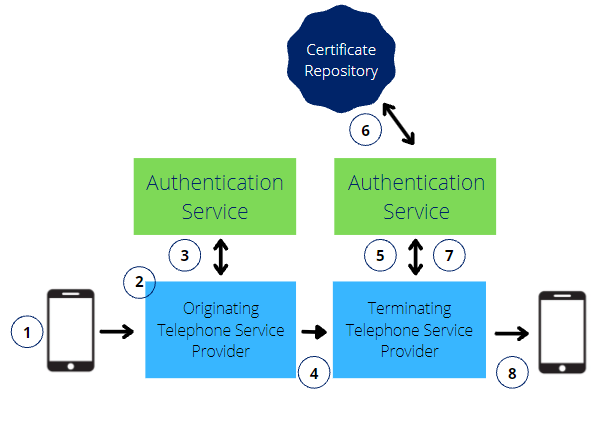
- A SIP INVITE is received by the originating telephone service provider.
- The originating telephone service provider checks the call source and calling number to determine how to attest for the validity of the calling number.
- Full Attestation. The service provider has authenticated the calling party and attest that they are authorized to the use the calling number. An example of this case is a subscriber registered with the originating telephone service provider’s softswitch.
- Partial Attestation. The service provider has authenticated the call origination but cannot verify the call source is authorized to use the calling number. An example of this use case is a telephone number behind an enterprise PBX.
- Gateway Attestation. The service provider has authenticated from where it received the call but cannot authenticate the call source. An example of this case would be a call received from an international gateway.
- The originating telephone service provider uses the authentication service to create a SIP Identity header. The authentication service could be a third party service hosted in the cloud, or a software application integrated with the telephone service provider’s Session Border Controller (SBC) or a softswitch. The SIP Identity header contains the following encrypted data:
- Calling number
- Called number
- Date and time
- Attestation
- Unique originating identifier
- The SIP INVITE with the SIP Identity header is sent to the terminating telephone service provider. In addition, the Identity token may be sent across the internet, around non-SIP call segments, using Out-of-Band SHAKEN.
- The SIP INVITE with Identity header is passed to the verification service.
- The verification service obtains the digital certificate of the originating telephone service provider from the public certificate repository. The two step process of verification commences. Verification is a two-step process. First, the SIP Identity header is base-64 decoded and the details are compared to the SIP INVITE message. If they match, the next step is to use the public key of the certificate to verify the SIP identity header signature. If both verification steps are successful, then the calling number has not been spoofed.
- The verification service returns the results to the terminating service provider’s softswitch or SBC.
- The call is completed to the called party.
More STIR/SHAKEN Information:
FCC/Implementation Dates and Information
Simplicity Joins With Top Communication Leader Verizon in Launching STIR/SHAKEN
STIR/SHAKEN Practical Impact
